Azure Key Vault made simple with Azure AD Managed Service Identity (MSI)
TL;DR - Azure Key Vault is hard but that's because you need to understand & implement the authentication with Azure AD. That's why Azure AD Managed Service Identity (MSI) now makes this a lot easier for you. There is no reason anymore not to use Azure Key Vault.
Update (29/07/2019) - Azure Managed Service Identity (MSI) is now called Azure Managed Identity (MI)
As you might know, I'm a big fan of Azure Key Vault - It allows me to securely store secrets and cryptographic keys while still having granular control on whom has access and what they can do.
Another benefit is that since all my secrets are centralized, it is easy to provide automatic rolling of authentication keys by simply updating the secrets during the process. If an application gets compromised or somebody has bad intentions, we can simply revoke their access and the secrets they have will no longer work.
If you want to learn more, you can read more in this article.
However, Azure Key Vault is heavily depending on Azure AD for handling the authentication & authorization and.
This means that in order to use Azure Key Vault, you not only need to understand how you use it, you also need to understand how AD works and what the authentication scheme is - And it ain't easy.
It is also hard to justify using Azure Key Vault as a secure store for all your secrets because instead of storing some of your secrets in an Azure Key Vault, you now need to store your AD authentication information instead. This can be via an authentication key or, preferably, a certificate that is being installed on you compute node instead.
Some actually see this as making the exposure bigger, which is true to a certain degree, because you are now basically storing the keys to the kingdom.
To conclude - Azure Key Vault itself is super easy to use, but the Azure AD part is not.
Introducing Azure AD Managed Service Identity
Azure AD Managed Service Identity (MSI) is a free turnkey solution that simplifies AD authentication by using your Azure resource that is hosting your application as an authentication proxy, if you will.
When enabling MSI, it will create an Azure AD Application for you behind the scenes that will be used as a "proxy application" which represents your specific Azure resources.
Once your application then authenticates on the local authentication endpoint, it will authenticate with Azure AD by its proxy application.
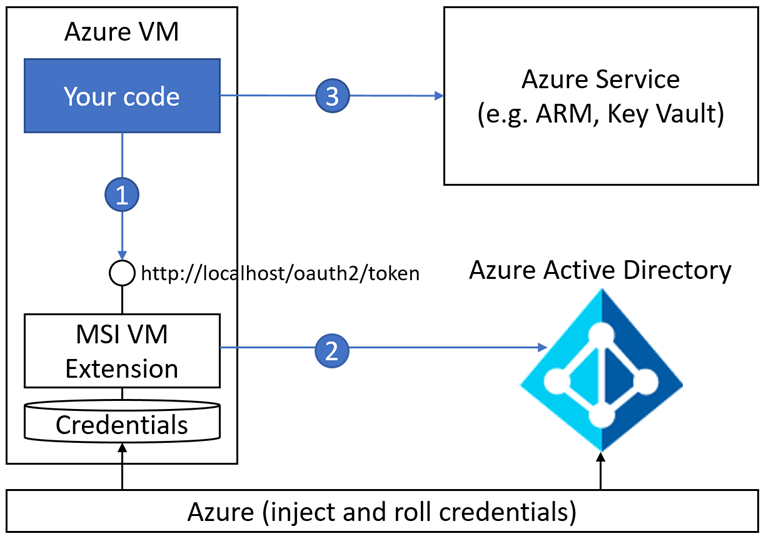
This means that instead of creating an Azure AD Application and granting it access to your resource, in our case Key Vault, you will instead only grant the proxy application access.
The best thing is - This is all abstracted for you which makes things very easy. You as a developer, just need to turn on MSI, grant the application access and you're good to go.
This turn key solution makes it super easy for developers to authenticate with Azure AD without knowing the details.
As Rahul explains in his post, you can use the AzureServiceTokenProvider from the Microsoft.Azure.Services.AppAuthentication NuGet package and let the magic do the authentication for you:
var azureServiceTokenProvider = new AzureServiceTokenProvider();
var keyVaultClient = new KeyVaultClient(new KeyVaultClient.AuthenticationCallback(azureServiceTokenProvider.KeyVaultTokenCallback));
var secretValue = await keyVaultClient.GetSecretAsync(VaultUri, secretName);
It would even be better if this would be built into the KeyVaultClient in the future so that it's more easy to discover and able to turn it on without any hassle.
Big step forward, but we're not there yet
While this is currently only in public preview, it's a big step forward for making authentication with AD dead simple but we're not there yet.
- AD Application Naming - One of the downsides is that it creates a new AD Application for you, with the same name as your Azure resource. This means that you are not able to pick an existing application or give it a descriptive name. This can be a blocker if you're using naming conventions.
- Support for limited resources - Currently MSI is only supported for Azure VMs, App Services & Functions. There are more services to come but if you're hoping for Azure Cloud Services, this is not going to happen unfortunately. A full overview is available in the documentation.
- Native support in Key Vault client - As mentioned before, it would be great if the Azure Key Vault SDK would support MSI out of the box without the need of doing anything ourselves from a coding perspective or need to be aware of the
Microsoft.Azure.Services.AppAuthentication - Feature Availability - It's still in preview, if you even care about that
Conclusion
With the introduction of Managed Service Identity there are no more reasons why you should not be using Azure Key Vault for your application anymore. It makes it a lot easier and you should aim to move all your secrets to Azure Key Vault.
It is great to see this evolution and have an easy way to do the authentication without making it complicated.
But Azure Key Vault is not the only service that integrates with AD that works well with MSI, other services like Azure Data Lake & SQL support this as well. You can get a full overview here.
I am very thrilled about Azure AD Managed Service Identity and will certainly use this, but there are some points for improvement.
Thanks for reading,
Tom
